Setting up Active Directory authentication
By default dbWatch authenticates users using it’s own internal username/password database. This
section describes how to add Active Directory as a second user authentication provider.
Connect to the server with the monitor with a privileged user. The default admin user has the right privileges.
In the monitor select AD configuration in the menu.

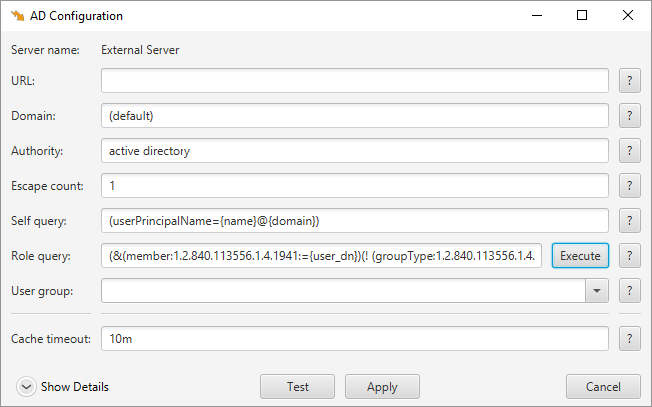
This opens the following dialog
- Url : The url of the domain controller. This url should start with either ldap:// or ldaps://
- Domain : The name of the domain used for authentication.
- Authority : Should be “active directory”
- Escape count : The number of times to escape backslash.
- Self query : The Active Directory query used to query for a users DN.
- Role query : The query used to query Active Directory for the groups containing the user.
- User group : The DN of the group used to controll login access to dbWatch. Only AD users that are members of this group wil be allowed to log in.
- Cache timeout : How long dbWatch should cache access privileges
Clicking “Execute” on the role query, will cause dbWatch to populate the “User group” selector with the avaialable groups found on the AD server.
For debugging purposes, the log from both the “Execute” and “Test” buttons will be available by clicking on “Show details”.
The Active Directory authentication process
The following process is applied to authenticate a user in dbWatch.
- The user enters his username and password in the logon dialog.
- The Monitor sends the username and password to the server.
- The server checks if the username + password matches the internal user database. If it matches the user is authenticated.
- The server tries to run the self-query against the active directory server using the username and password provided by the Monitor. This provides the users DN whitch is used in the next step.
- The server applies the users DN to the role-query. The resulting query is then run against the active directory server using the username and password provided by the Monitor. The result is converted to a list of dbWatch roles which is applied to the user.
- If the result contains the user-group the user is authenticated.
- If any of the roles returned by the roles query exist in dbWatch they are temberarily granted to the user.
The user group.
The user group is used to filter whitch AD users are allowed to log in to dbwatch. In order to be allowed to log in the user must be a member of this SD group.
The string must be the groups DN. Whitch is usually on the form “CN=..,CN=…”.
Available from dbWatch version 12.2 the user group has a few more possibilities.
- If the user-group field is left empty. All users with a AD login will be able to log in to dbWatch.
- If the user-group field does not contain “cn=” it will be treated as a plain text name of a group. DbWatch will treat all groups containing cn=<> as the user-group.
- if the user-group contains “cn=” it will be treated as the full DN of the user group.
Mapping Active Directory groups to roles
When a user logs in with AD the system looks for roles matching the group memberships of the user. If any matching roles are
defined in dbWatch they are granted to the user for as long as the authentication is cached.
Any AD groups not connected to a dbWatch role will be remembered by dbWatch and will appear in the operator dialog as sugested roles. These are marked with gray text.
After logging in with the user “user1” which is mamber of the two groups “CN=Domain Users,CN=Users” and “CN=dbWatchUsers,CN=Users” the operator dialog looks like this

It is then possible to select one of the roles and add grants to it.
Optimizing AD performence
In some configurations the query used to determine the roles of a user can be slow. The default query
is recursive and returns all groups the user is a member of. Including indirect memberships.
If you experience a performance hit on the AD server you can set the role-query to (&(objectCategory=group)(member={user_dn}))
This query only asks for direct group memberships, but is much faster. Increasing the cache timeout will also decrease the load on the AD server.


Post your comment on this topic.