Internal Control Center Firewall
Overview
The built-in firewall in dbWatch Control Center provides an additional layer of security, particularly useful in distributed environments or when exposing nodes to untrusted networks (e.g., internet-facing cloud routers or DMZ setups).
This internal firewall allows precise control over:
- Which IPs can connect to a node
- Which domains the node may forward certificates for
- Whether or not domain discovery information is advertised
The firewall is configured per node through the Domain Configuration Dialog.
Accessing the Firewall Configuration
To configure the firewall for a node:
- Open the Domain Configuration dialog
- Select the node you want to configure
- Click “Firewall Configuration”
Launching the configuration window:
The Firewall GUI is divided into three sections:
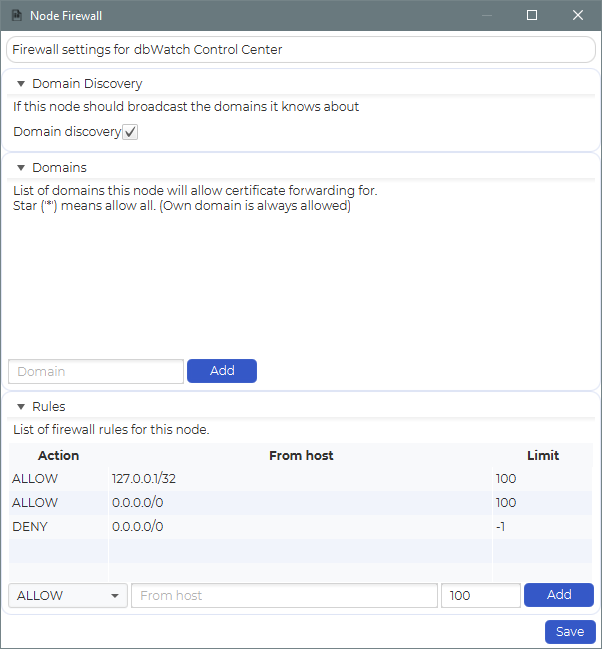
Section 1: Domain Discovery
Domain Discovery governs whether a node will publicly list its known domains during connection attempts.
- When enabled: The node advertises its known domains, allowing clients or monitors to choose one from a dropdown.
- When disabled: Users must manually specify the domain name, improving security by reducing exposure.
This is especially useful when setting up security-hardened environments with limited visibility.
Section 2: Domains
This section defines which domains this node is allowed to forward certificates for.
This configuration is essential for cloud routers or multi-domain nodes. It ensures routing behavior is strictly scoped to expected domain memberships, reducing potential for misrouting or lateral movement across domains.
Section 3: Rules (IP Access Control)
The Rules section enables you to define IP-based access control policies using CIDR notation.
Each rule includes:
- Action – ALLOW or DENY
- From host – An IP or CIDR range
- Limit – Max concurrent connections allowed from this source (set to -1 for unlimited or deny)
Default rule set:
| Action | From host | Limit |
| ---------- | -------------- | -------- |
| ALLOW | 127.0.0.1/32 | 100 |
| ALLOW | 0.0.0.0/0 | 100 |
| DENY | 0.0.0.0/0 | -1 |
Explanation:
- Rule 1 explicitly allows connections from localhost with a max of 100 concurrent sessions.
- Rule 2 allows all other IPs globally (intended for demo or dev usage).
- Rule 3 is a fail-safe deny rule, ensuring that connections not matched earlier are rejected.
> To enhance security, it is recommended to replace the 0.0.0.0/0 rule with more specific subnets using CIDR notation:
>
> * Example: `192.168.0.0/24` for the 192.168.0.* range
> * Example: `192.168.0.3/32` to allow only a single IP
Best Practices
- Always review and restrict the Domains list on cloud routers to avoid unintended routing
- Use fine-grained CIDR filtering for Rules instead of broad 0.0.0.0/0 rules
- Disable Domain Discovery for enhanced privacy when nodes are exposed to untrusted networks
- Combine firewall filtering with certificate validation for layered defense
- Test connectivity after making changes to confirm intended access behavior