Certificate Infrastructure
dbWatch Control Center uses an internal public key infrastructure (PKI) to ensure secure communication, identity management, configuration integrity, and access control across all nodes and users in the domain.
Each Control Center domain operates its own certificate authority (CA) that issues and manages certificates for server nodes, clients, users, and configuration files.
To fully understand how the certificate infrastructure supports secure communication, see the Core Concepts & Architecture overview.
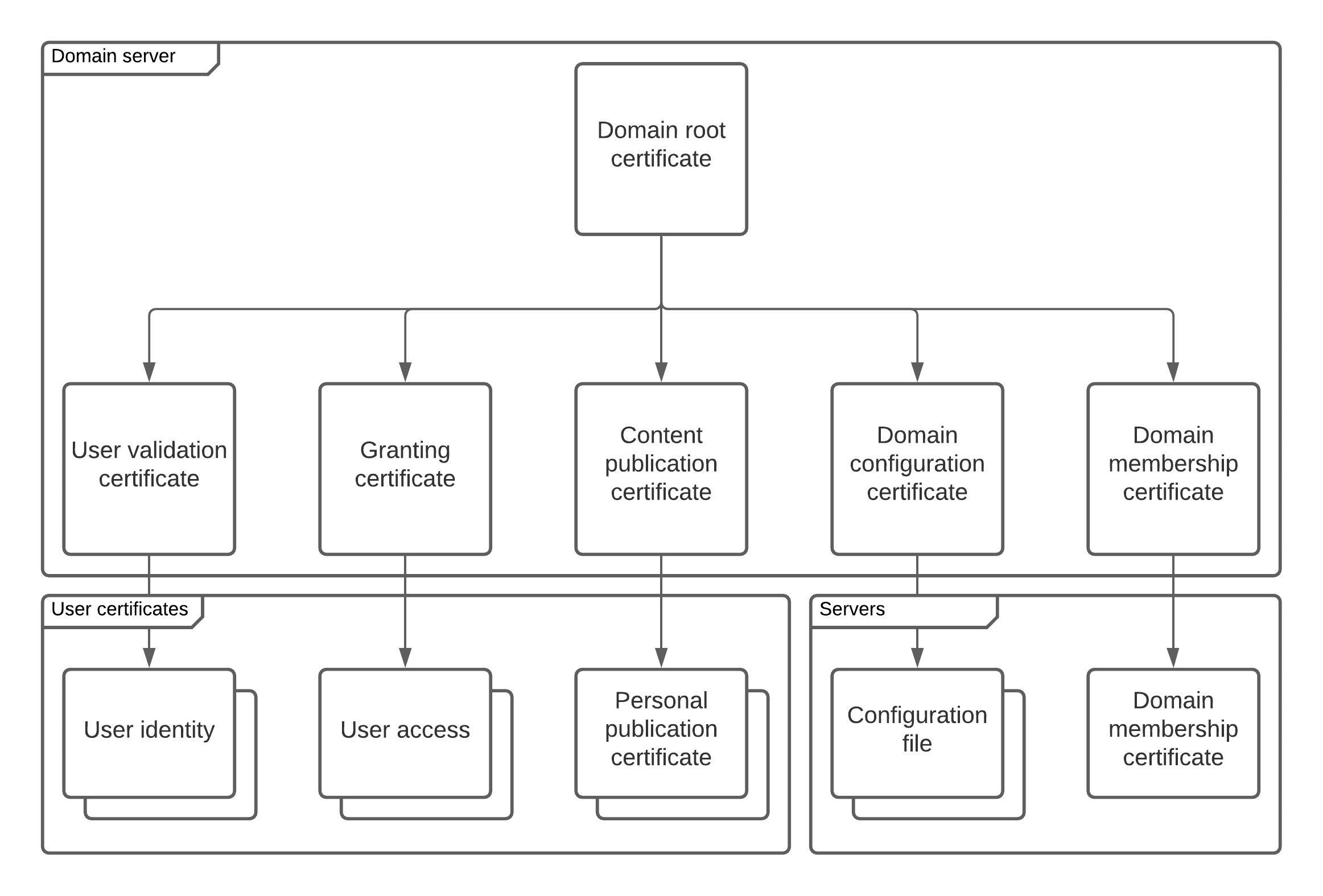
Domain Root Certificate
The Domain Root Certificate is the trust anchor for the entire dbWatch Control Center domain. It:
- Acts as the Certificate Authority (CA) for all issued certificates
- Is self-signed by default, but can be signed by dbWatch AS for external trust scenarios
- Is required to bootstrap trust between nodes (server, monitor, client)
> If a domain’s root certificate is compromised, all trust relationships must be revoked and re-established.
User Identity Certificate
This certificate is used by the domain CA to sign user certificate requests. It ensures:
- That each user identity is cryptographically verifiable
- That Control Center clients only accept users with valid, domain-issued credentials
- Secure authentication and authorization within the UI or command-line (CCC)
Granting Certificate
The Granting Certificate is used by the domain to:
- Sign user permission assignments
- Validate access rights for roles, instances, and modules
- Ensure that privilege changes are authorized and verifiable
This enables strong role-based access control (RBAC) backed by cryptographic assurance.
Configuration Certificate
The Configuration Certificate is used to sign system-wide settings, such as:
- Node configuration files
- Job deployment templates
- Credential distribution
This ensures configuration integrity during replication or rollout to other nodes. Tampering with a signed configuration will result in a validation failure.
Publication Certificate
The Publication Certificate is used to:
- Digitally sign reports, exports, or published datasets generated by Control Center
- Ensure data authenticity when sent to external systems (e.g., emailed reports, dashboard exports)
- Optionally verify the origin of reports if audited or received via third-party systems
Security and Trust Model
All certificates are managed within the dbWatch Control Center domain and:
- Stored securely on the primary server node
- Distributed to clients and monitor nodes during controlled registration
- Validated at connection time between all nodes
- Automatically revoked if a node is deregistered or removed
No external certificate authority is required unless cross-domain trust or third-party integration demands it.
Recommendations
- Keep the domain root certificate and private key secure and backed up
- Use strong passphrases and limited-access storage for certificates
- Rotate certificates periodically or immediately upon compromise
- Do not share domain certificates between unrelated environments
- Enable audit logging for certificate events and domain changes
Related Topics
For advanced certificate management or trust configuration in segmented environments, contact:
support@dbwatch.com