Encryption
dbWatch Control Center applies strong encryption practices to ensure secure communication between all components within a Control Center domain, including servers, monitor nodes, and clients.
End-to-End Encrypted Communication
All network traffic exchanged between dbWatch server nodes and monitor clients is end-to-end encrypted using:
- Symmetric encryption with AES/GCM (256-bit keys)
- Authenticated encryption to protect both confidentiality and integrity of messages
- Key exchange through Elliptic-curve Diffie-Hellman (ECDH) negotiation
The use of AES-GCM provides high-performance encryption while also embedding verification to prevent tampering.
Node Certificate-Based Encryption
Encryption keys are derived from certificates issued by the domain’s internal Certificate Authority (CA), which are managed through the dbWatch certificate infrastructure.
Each communication session:
- Authenticates participating nodes using certificates
- Negotiates a session key via ECDH
- Encrypts all data using the negotiated session key with AES/GCM
Read more about the certificate infrastructure:
Certificate Infrastructure
Certificate-Based Signing and Ephemeral Keys
To ensure strong identity and message integrity, dbWatch uses digital signatures and temporary session keys:
- Messages are signed with SHA256withECDSA (Elliptic Curve Digital Signature Algorithm)
- Ephemeral signing certificates are automatically regenerated every 10 minutes
- This reduces exposure time in the event of certificate compromise
You can view certificate rotation in real time via:
Help → Debug → Certificates
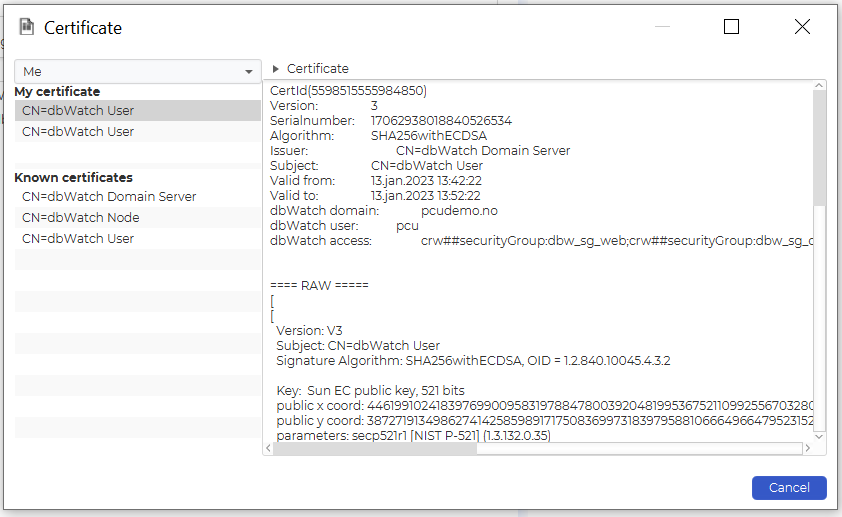
Debugging and Verifying Encryption
You can verify encryption details during an active session via:
Help → Debug → Connection Info
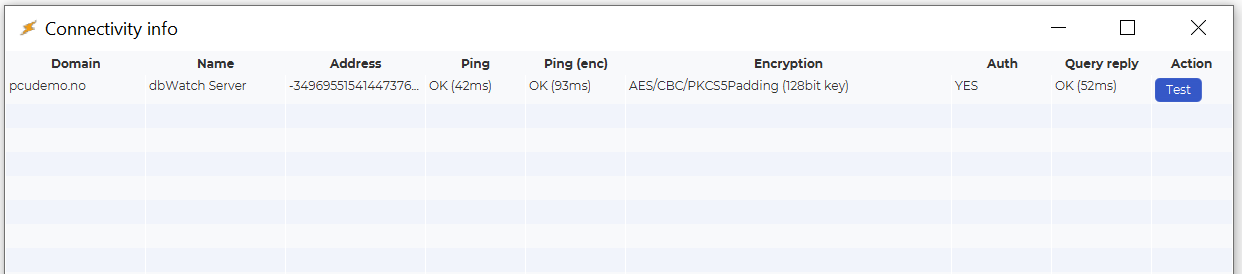
This window shows:
- Connection status and encryption protocols
- Certificate subjects and issuers
- Session-specific key exchange parameters
Protocol Summary
| Layer | Mechanism |
|---|---|
| TLS transport | AES/GCM with 256-bit symmetric keys |
| Key exchange | Elliptic-curve Diffie-Hellman |
| Signing | SHA256withECDSA |
| Certificate rotation | Every 10 minutes (ephemeral certs) |
Security Recommendations
- Use only nodes with valid certificates issued by your domain CA
- Do not reuse certificates between environments
- Use the built-in debug tools to regularly verify encryption and certificate status
- Disable unused ports and configure internal firewall for IP restrictions
Related Topics
For questions regarding encryption standards or enabling advanced cryptographic settings, contact:
support@dbwatch.com